Operating Systems: Theory and Design
Jacob Harrison
CPT 304 Final Project
Dr. Limon
06/01/2019
I
always believed that an operating system magically makes a computer work. I
never realized there were so many "moving pieces" to the creation and
implementation of an operating system. This paper will set out to describe the
five major components of an operating system, with diagrams included to further
enhance the understanding of the concepts.
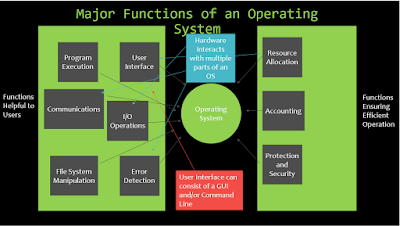
It's
essential that we examine the primary functions of an operating system. The
text we studied for this course listed nine; six built to make life easier for
the user and three that ensure efficient operation (Silberschatz, Galvin, &
Gagne, 2014). The six that make our lives easier consist of Program Execution,
User Interface, I/O operations, File System Manipulation, Error Detection, and
Communications. The three that make sure our computers run efficiently are
Resource Allocation, Accounting, and Protection and Security. Here's a further
explanation of each. Program execution is where the OS loads a program into
memory and executes instructions. The User Interface will usually consist of a
GUI such as Windows and/or command line. I/O Operations allow the user to
interact with the OS and File System Manipulation enables files in memory to be
read, edited, moved, deleted, etc. Error Detection is the OS's ability to
detect and correct errors as they arise. Finally, Communications allows
processes to communicate and share information.
As
for the final three, resource allocation manages resources dependent upon what
resources users are using. Accounting keeps a record of resources being used by
a user for statistics. Finally, Protection and Security monitors traffic and
keeps logs of suspicious activities. Here's a chaotic diagram separating the
different functions.
Next, we dig a little deeper and discuss threads and synchronization.
Let's discuss what a process is. A process is a program being executed. The
process states consist of New, Running, Waiting, Ready, and Terminated. New is
when the process is created. Running is when the instructions are being
executed. Waiting is when the process is waiting on some kind of event to
happen. Ready, the process is prepared to be assigned to a processor. Finally,
Terminated is when the process has completed. The PCB, or Process Control
Block, holds information related to each process (Silberschatz, Galvin, &
Gagne, 2014).
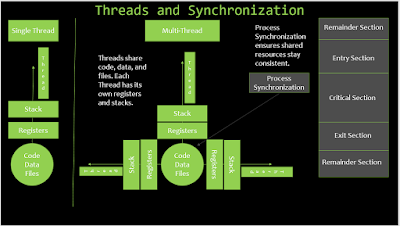
After processes, we should discuss threading. Each thread consists of
code, data, and files. Also, each thread has its own stack and registers. In a
single thread, the thread operates by itself. With multi-threads, the threads
share the code, data, and files. Process Synchronization helps to ensure that
all shared resources stay consistent.
Finally, the critical section is part of the process synchronization. The
critical section is the part of the code that updates common variables, writing
a file, etc. No two process can be in their critical sections at the same time,
to ensure shard data stays consistent. Here's a diagram that's a little less
cluttered.
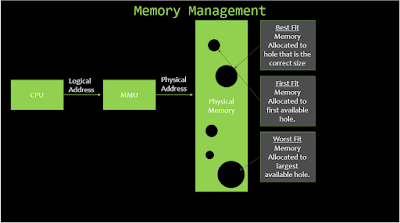
Now
that we've discussed threads and synchronization let's look at memory
management. There are two parts to the memory, virtual space, and physical
memory. Virtual address space is it is the part of the memory where a program
believes it is running. The CPU helps to generate the address. The memory
management unit helps to translate the processes into the physical memory where
it is stored. There are three ways that items are stored into memory holes;
first fit, best fit, and worst fit. With first fit, memory is stored in
the first hole that it will fit in. With best fit, it's stored in the hole that
matches the closest to the size of the file, and with worst fit, memory is stored
in the largest available hole. Fragmentation is what happens as files leave
small holes in the memory that are unable to be filled, causing the computer to
possibly run slow as it looks for a spot to place the file. Systems should
check for fragmentation regularly to ensure that the memory is being used
efficiently. Take a gander at this picture describing memory management.
Let's move
on to discuss file management, directories, and I/O devices. Computers use file
management to maintain the user's files in a neat and orderly fashion. Data can
be saved in different locations such as flash memory or slower, secondary
memory like the hard disk.
Multiple
file directory systems can be used such as, single and two level directories,
tree structures, acyclic graph directories, and general graph directories. The
tree-based directory structure Windows uses seems like the most common way to
lay out the files in a system. File protection is another concept to consider.
Because a majority of the user's information is stored in secondary storage,
it's important that the files remain safe and free and corruption. Here's a
graph demonstrating a tree directory structure.
As
for the different types of I/O devices, there are a few that interact in
various ways with the computer. There are storage devices like jump drives and
hard drives. There are a few devices that help send information, like Bluetooth
and network connections. Then there are items like a keyboard and mouse,
devices that allow the user to interact with the computer. Using different
kinds of connections, like a bus connection or cables, instructions from the
I/O devices are converted to computer instructions and are carried out by the
OS.
Finally, we come to security and protection. The slide for this section
lists the types of security risks that both programs, networks, and systems
face as well as some preventable measures that can be taken to ensure the
safety of the machines.
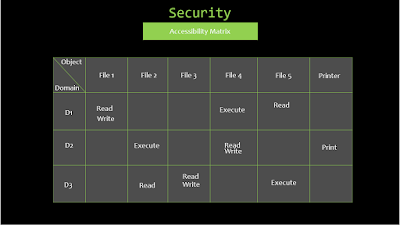
One
of the best tools that can be used to secure a system is an accessibility
matrix. The accessibility matrix creates a visual representation of what access
different users have to different parts of a system. The access each user has
can be assigned based by roles or needs to access different files.
Here's one final picture to bring all these ideas together.
Let's wrap this up! At
the beginning of the course, nearly five weeks ago, I believed I had a pretty
good understanding of how operating systems work, especially Windows, Android,
and iOS as those are the systems I use daily. I honestly wasn't prepared for
the amount of information I would receive, it's been a roller coaster! While
I've found it challenging to follow some concepts, I've gained a much deeper
appreciation for just how hard our computers work for us and how intricate
their designs are. As computing becomes faster and the necessity for processes
to happen instantly increase, the way our operating systems handle everything
will only get more complicated. I can see the operating systems of the future
working at blazing fast speeds, solving the most challenging problems, and
possibly knowing what we want before we want it. I can't wait to see where we
go from here!
References:
Silberschatz, A., Galvin, P. B., & Gagne, G. (2014). Operating system concepts essentials (2nd ed.). Retrieved from https://redshelf.com/




No comments:
Post a Comment